Bitdefender regularly audits popular IoT hardware for vulnerabilities.
This research paper is part of a broader program that aims to shed light on the security of the world’s best-sellers in the IoT space.
This report covers vulnerabilities discovered while researching the LG WebOS TV operating system.
Bitdefender has found several issues affecting WebOS versions 4 through 7 running on LG TVs.
These vulnerabilities let us gain root access on the TV after bypassing the authorization mechanism.
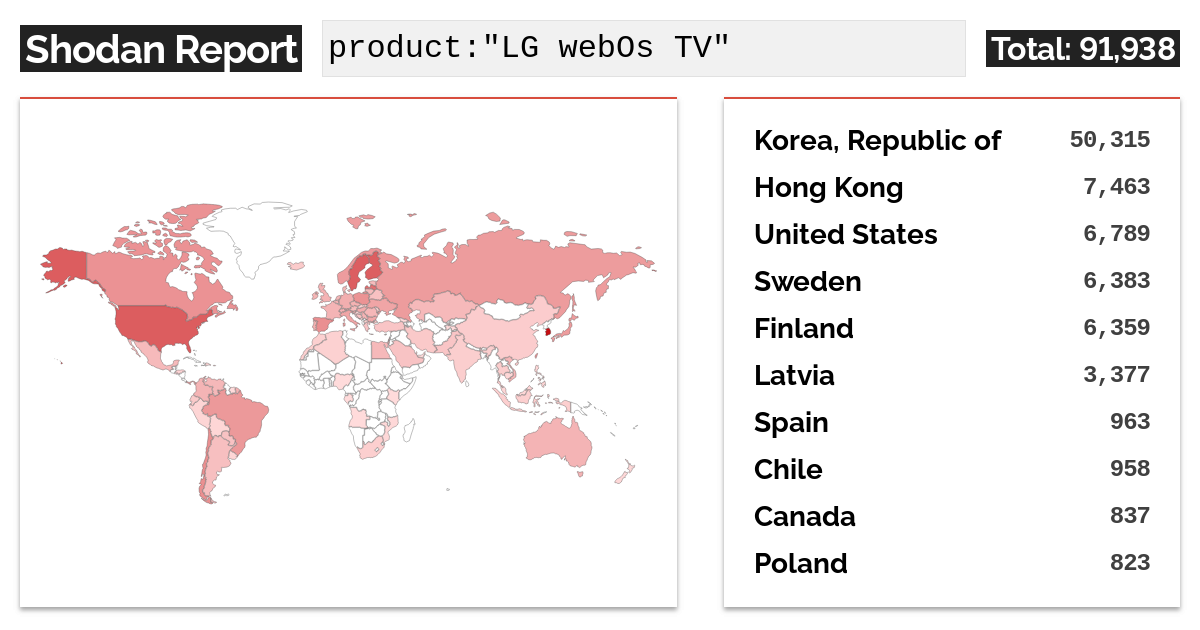
Although the vulnerable service is intended for LAN access only, Shodan, the search engine for Internet-connected devices, identified over 91,000 devices that expose this service to the Internet.
Vulnerabilities at a glance
- Bitdefender researchers discovered a vulnerability that lets an attacker bypass the authorization mechanism in WebOS versions 4 through 7. By setting a variable, the attacker can add an extra user to the TV set (CVE-2023-6317)
- Another vulnerability allows attackers to elevate the access they gained in the first step to root and fully take over the device (CVE-2023-6318)
- A third vulnerability (CVE-2023-6319) allows operating system command injection by manipulating a library responsible with showing music lyrics.
- The CVE-2023-6320 vulnerability lets an attacker inject authenticated commands by manipulating the com.webos.service.connectionmanager/tv/setVlanStaticAddress API endpoint.
Vulnerable OS versions
- webOS 4.9.7 – 5.30.40 running on LG43UM7000PLA
- webOS 5.5.0 – 04.50.51 running on OLED55CXPUA
- webOS 6.3.3-442 (kisscurl-kinglake) – 03.36.50 running on OLED48C1PUB
- webOS 7.3.1-43 (mullet-mebin) – 03.33.85 running on OLED55A23LA
Disclosure timeline
- Nov 01, 2023: Vendor disclosure
- Nov 15, 2023: Vendor confirms the vulnerabilities.
- Dec 14, 2023: Vendor requests extension
- Mar 22, 2024: Patch release
- Apr 09, 2024: Public release of this report
A technical look into the discovered vulnerabilities
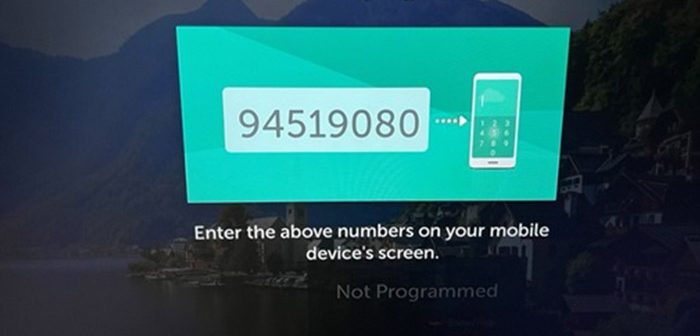
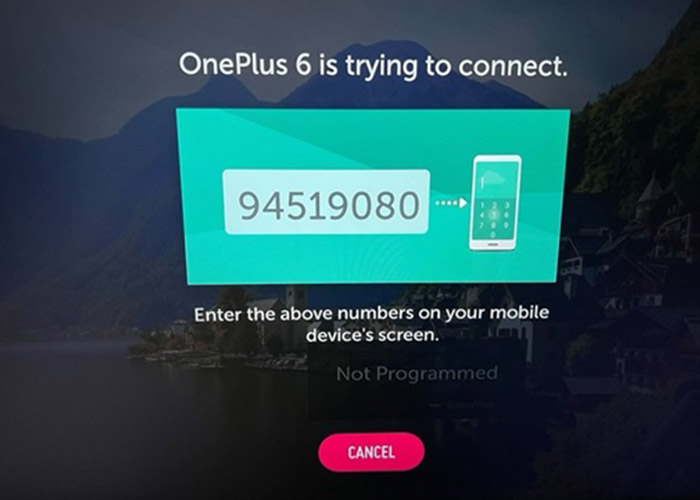
WebOS runs a service on ports 3000/3001 (HTTP/HTTPS/WSS) which is used by the LG ThinkQ smartphone app to control the TV.
To set up the app, the user must enter a PIN code into the display on the TV screen.
An error in the account handler lets an attacker skip the PIN verification entirely and create a privileged user profile.
The function that handles account registration requests uses a variable called skipPrompt which is set to true when either the client-key or the companion-client-key parameters correspond to an existing profile.
It also takes into consideration what permissions are requested when deciding whether to prompt the user for a PIN, as confirmation is not required in some cases.
We can request the creation of an account with no permissions, which will be automatically granted. Then we request another account with elevated permissions, but we specify the companion-client-key variable to match the key we got when we created the first account. The server will confirm that this key exists but will not verify if it belongs to the correct account. Thus, the skipPrompt variable will be true and the account will be created without requesting a PIN confirmation on the TV.
This vulnerability, identified as CVE-2023-6317, has been confirmed to affect webOS 4.9.7, 5.5.0, 6.3.3-442, and 7.3.1-43.
Having created a privileged account without user interaction, we now have access to a large attack surface that was inaccessible before. We have found two authenticated command injection vulnerabilities that lead to root access, and another that runs commands as the dbus user.
Authenticated command injection in the processAnalyticsReport method from the com.webos.service.cloudupload service
The processAnalyticsReport method requires three parameters: type, reportFile, and originalFile. When the type parameter is set to “analytic” the reportFile parameter will be passed to a system command without being sanitized.
Although requests to this method cannot be performed directly, we can use another endpoint, system.notifications/createAlert, to bypass this restriction, accessible only to authenticated users who have the WRITE_NOTIFICATION_TOAST permission. The onclose parameter supported by this endpoint allows us to perform internal requests to services that are not exposed, similar to SSRF. After we create the notification, we trigger the onclose call through the system.notifications/closeAlert endpoint, performing the request to the vulnerable endpoint.
The specified file must exist on the device, but we can bypass this constraint by using the download method from the com.webos.service.downloadmanager service, which will create a file in the /media/internal/downloads/ directory with an arbitrary filename. Both the processAnalyticsReport and download methods can be accessed through the createAlert endpoint.
The vulnerable command is created on line 83 and executed on line 84:
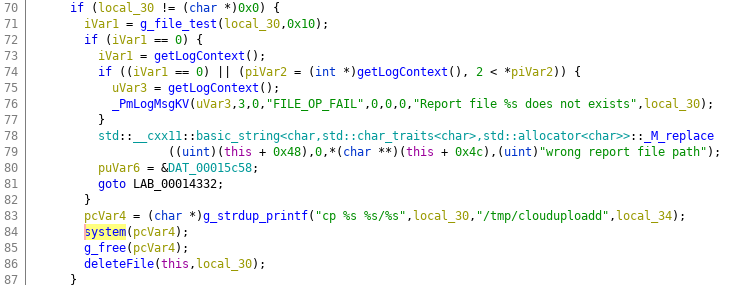
This vulnerability, identified as CVE-2023-6318, has been confirmed to affect webOS 5.5.0, 6.3.3-442, and 7.3.1-43.
Authenticated command injection in the getAudioMetadata method from the com.webos.service.attachedstoragemanager service
The getAudioMetadata method requires two parameters: deviceId and fullPath. While the deviceId parameter is not important, the fullPath parameter will be passed, under certain conditions, to a system command without being sanitized. If this parameter points to a file with the .mp3 extension the service will search in the same directory for the corresponding lyrics file with the same name (.lrc extension). If found, the first four bytes of the lyrics file will be compared with the sequence \xFF\xFE\x00\x00. If they match (meaning that the file is UTF1632 encoded) the service will try to decode it using the iconv binary. This binary will be called together with the full filename without prior sanitization, leading to command injection.
Both the .mp3 and .lrc files must exist on the device and can be created using the download method mentioned earlier. All required methods can be accessed through the createAlert endpoint.
The vulnerable code in convLrcStringByBinary from the asm binary:

This vulnerability, identified as CVE-2023-6319, has been confirmed to affect webOS 4.9.7, 5.5.0, 6.3.3-442, and 7.3.1-43.
Authenticated command injection in the com.webos.service.connectionmanager/tv/setVlanStaticAddress endpoint allows execution of commands on the device as dbus
The setVlanStaticAddress endpoint requires three parameters: ip_address, bcast_address, and netmask. All three parameters will be passed to a system command without being sanitized. Before calling this endpoint, we must first call the createVirtualLan endpoint. These endpoints require the READ_NETWORK_STATE permission.
Although the user that executes the commands is dbus, this account has similar permissions as the root user.
Vulnerable code in handle_set_vlan_static_address_command from libwca2.so library:
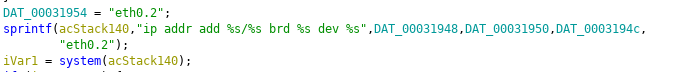
This vulnerability, identified as CVE-2023-6320, has been confirmed to affect webOS 5.5.0 and 6.3.3-442.